“STOP” Ransomware
Original Issue Date:-
February 25, 2020
Virus Type:-
Ransomware
Severity:-
High
CERT-In has observed a new variant of "STOP" ransomware is spreading widely. Once the victim computer is infiltrated with STOP ransomware, all files are encrypted and an extension “.stop” is appended to the encrypted iles at the end. After encrypting all the files, ransomware will also delete the Shadow Volume Copies so that recovery is not possible.

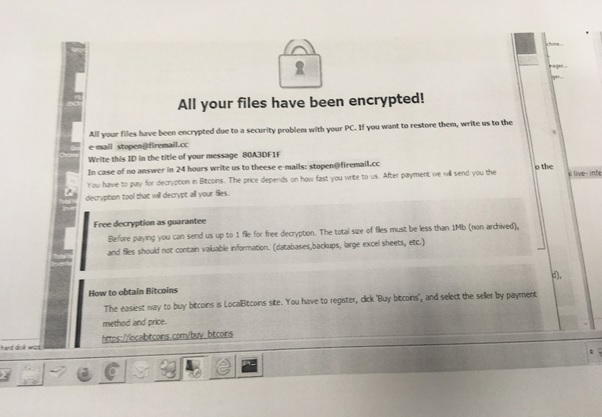
After encrypting, STOP malware generates a ransom note file “!!! YourDataRestore !!! txt” which contains the message asking for ransom from the victim to decrypt their encrypted data. Ransom note provides an email address for communication.
The ransomware campaign uses Spear Phishing, Social Engineering, Browser Targeted Code Injection and Abuse of Application Functionality as its attack vectors. The ransomware is exploiting flowing vulnerabilities mainly belonging to Buffer overflow, Remote Code Execution and Windows Denial of Service categories (CVE-2016-10057, CVE-2016-10401, CVE-2017-0144, CVE-2017-10271, CVE-2017-12149, CVE-2018-0986, CVE-2018-1000136, CVE-2018-10115, CVE-2018-20250, CVE-2018-3639, CVE-2018-5383, CVE-2018-5391, CVE-2018-6789, CVE-2018-7602, CVE-2018-9995, CWE-119, CWE-19, CWE-20, CWE-200, CWE-22, CWE-255, CWE-284, CWE-310, CWE-347, CWE-502).
Appended file extensions:
- .STOP
- .SUSPENDED
- .WAITING
- .CONTACTUS
- .DATASTOP
- .PAUSA
- .KEYPASS
- .WHY
- .SAVEfiles
- .DATAWAIT
- .INFOWAIT
- .puma
- .pumax
- .pumas
- .shadow
- .djvu
- .djvuu
- .djvus
- .udjvu
- .uudjvu
- .kroput1
- .charck
- .kropun
- .doples
- .luces
- .luceq
- .chech
- .pulsar1
- .proden
- .tocue
- .daris
- .gusau
- .madek
- .lapoi
- .todar
- .dodoc
- .novasof
- .bopador
- .ntuseg
- .ndarod
The ransom message includes following email addresses:
- stopen[at]firemail.cc
- deathransom[at]airmail.cc
- keypass[at]bitmessage.ch
- keypass[at]india.com
- last_centurion[at]aol.com
- makdonalds[at]india.com
- savefiles[at]india.com
- servicedeskpay[at]protonmail.com
- stopfilesrestore[at]bitmessage.ch
- topfilesrestore[at]india.com
- suspendedfiles[at]bitmessage.ch
- suspendedfiles[at]india.com
- decryption[at]bitmessage.ch
- BM-2cUMY51WfNRG8jGrWcMzTASeUGX84yX741[at]bitmessage.ch
- keypassdecrypt[at]india.com
Following are some steps which can be taken to prevent further such Infections:
- Perform regular backups of all critical information to limit the Impact of data or system loss and to help expedite the recovery process. Ideally, this data should be kept on a separate device, and backups should be stored offline.
- Keep the operating system third party applications (MS Office, browsers, browser Plugins) up-to-date with the latest patches.
- Maintain updated Antivirus software on all systems.
- Don't open attachments in unsolicited e-mails, even if they come from people in your contact list, and never click on a URL contained in an unsolicited e-mail, even if the link seems benign. In cases of genuine URLs ,close out the e-mail and go to the organization's website directly through the browser.
Best Practices and Recommendations to protect users against the threat of ransomware:
- Update software and operating systems with the latest patches. Outdated applications and operating systems are the targets of most attacks.
- Scan all incoming and outgoing emails to detect threats and filter executable files from reaching end users.
- Network segmentation and segregation into security zones - help protect sensitive information and critical services. Separate administrative network from business processes with physical controls and Virtual Local Area Networks.
- Restrict users’ permissions to install and run software applications, and apply the principle of “least privilege” to all systems and services. Restricting these privileges may prevent malware from running or limit its capability to spread through a network.
- Configure firewalls to block access to known malicious IP addresses.
- Users are advised to disable their RDP if not in use, if required it should be placed behind the firewall and users are to bind with proper policies while using the RDP.
- Restrict execution of Power shell /WSCRIPT in enterprise environment Ensure installation and use of the latest version of PowerShell, with enhanced logging enabled.
Script block logging and transcription enabled. Send the associated logs to a centralized log repository for monitoring and analysis.
https://www.fireeye.com/blog/threat-research/2016/02/greater_visibilityt.html - Establish a Sender Policy Framework (SPF) for your domain, which is an email validation system designed to prevent spam by detecting email spoofing by which most of the ransomware samples successfully reaches the corporate email boxes.
- Application whitelisting/Strict implementation of Software Restriction Policies (SRP) to block binaries running from %APPDATA% and %TEMP% paths. Ransomware sample drops and executes generally from these locations.
- Don't open attachments in unsolicited e-mails, even if they come from people in your contact list, and never click on a URL contained in an unsolicited e-mail, even if the link seems benign. In cases of genuine URLs close out the e-mail and go to the organization's website directly through browser.
- Block the attachments of file types, exe|pif|tmp|url|vb|vbe|scr|reg|cer|pst|cmd|com|bat|dll|dat|hlp|hta|js|wsf consider encrypting the confidential data as the ransomware generally targets common file types.
- Carry out vulnerability Assessment and Penetration Testing (VAPT) and information security audit of critical networks/systems, especially database servers from CERT-IN empanelled auditors. Repeat audits at regular intervals.
- Perform regular backups of all critical information to limit the impact of data or system loss and to help expedite the recovery process. Ideally, this data should be kept on a separate device, and backups should be stored offline.
Generic Prevention Tools:
- Sophos: Hitman.Pro
https://www.hitmanpro.com/en-us/surfright/alert.aspx - Malwarebytes Anti-Ransomware (formally Crypto Monitor)
https://blog.malwarebytes.com/malwarebytes-news/2016/01/introducing-the-malwarebytes-anti-ransomware-beta/ - Trendmicro Ransomware Screen Unlocker tool:
https://esupport.trendmicro.com/en-us/home/pages/technical-support/1105975.aspx - Microsoft Enhanced mitigation and experience toolkit(EMET)
https://www.microsoft.com/en-us/download/details.aspx?id=50766 - Quick Heal
http://www.quickheal.com/free-ransomware-decryption-tool/ - Trend Micro (Trend-micro-ransomware-file-decryptor)
https://success.trendmicro.com/solution/1114221-downloading-and-using-the-trend-micro-ransomware-file-decryptor
References:


