Android: EventBot Malware (Banking Trojan)
Original Issue Date:- May 08, 2020
Virus Type:- Banking Trojan
Severity:- Low
It has been observed that a new android mobile malware named EventBot is spreading. It is a Mobile banking trojan and infostealer that abuses Android’s in-built accessibility features to steal user data from financial applications, read user SMS messages and intercepts SMS messages allowing malware to bypass two-factor authentication.
EventBot targets over 200 different financial applications including banking applications, money transfer services and cryptocurrency wallets/ financial applications based in US and Europe region at the moment but the some services may affect Indian users as well. EventBot largely targeting financial applications like Paypal Business, Revolut, Barclays, UniCredit, CapitalOne UK, HSBC UK, TransferWise, Coinbase, paysafecard etc.
Infection mechanism:
EventBot is not seen on Google Playstore yet, it uses several icons to masquerade as a legitimate application such as Microsoft Word, Adobe flash etc. and using third party application downloading sites to infiltrate into victim device.
Once installed on victim’s Android device, it asks permissions such as controlling system alerts, reading external storage content, installing additional packages, accessing internet, whitelisting it to ignore battery optimizations, prevent processor from sleeping or dimming the screen, auto-initiate upon reboot, and receive and read SMS messages, continue running and accessing data in the background. Further, it prompts user to give access to device’s accessibility services. Also, it can retrieve notifications about other installed applications and read contents of other applications. Over the time It can also read LockScreen and in-app PIN that can give attacker more privileged access over victim device.
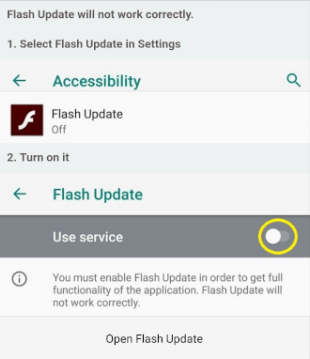
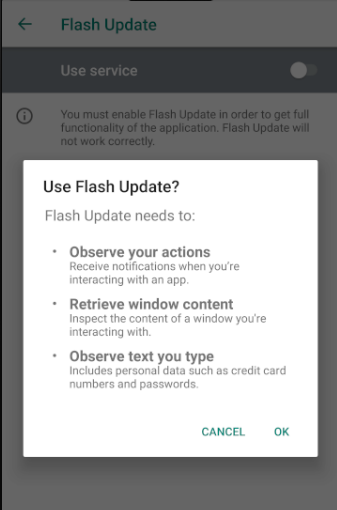
EventBot downloads and updates configuration file with almost 200 different financial application targets. HTTP response received from C2 server is encrypted with Base64 and RC4 encryption.
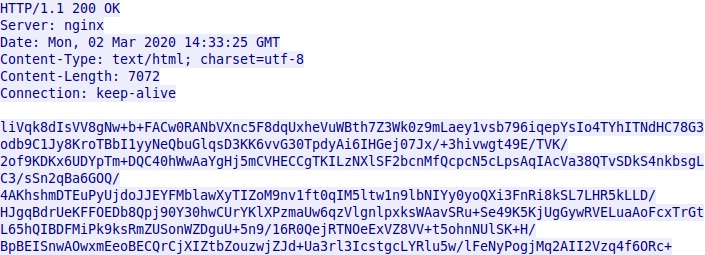
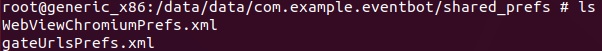
EventBot uses multiple tactics to exploit accessibility events for webinjects and other information stealing purposes. EventBot has method called parseCommand that can update its configuration XML files located in shared preferences folder on the device.
Malware Infrastructure:
A repeated pattern identified based on the specific URL gate_cb8a5aea1ab302f0_c after mapping of C2 servers. Also, a potential link with an another infostealer was identified. The IP address of two domains; ora.carlaarrabitoarchitetto[.]com and ora.studiolegalebasili[.]com, is 31.214.157[.]6. This IP was previously hosting a domain next.nextuptravel[.]com, which was the C2 for an Android infostealer responsible for several attacks in past.
IOC:
C2 IP:
- 185.158.249[.]141
- 185.158.248[.]102
- 50.63.202[.]81
- 185.158.248[.]102
- 31.214.157[.]6
- 208.91.197[.]91
C2 Domain URLs:
- http://themoil[.]site/gate_cb8a5aea1ab302f0_c
- http://pub.douglasshome[.]com/gate_cb8a5aea1ab302f0_c
- http://ora.carlaarrabitoarchitetto[.]com/gate_cb8a5aea1ab302f0
- http://ora.carlaarrabitoarchitetto[.]com/gate_cb8a5aea1ab302f0_b
- http://marta.martatovaglieri[.]it/gate_cb8a5aea1ab302f0_c
- http://free.timberlinetraders[.]com/gate_cb8a5aea1ab302f0_c
- http://ora.studiolegalebasili[.]com/gate_cb8a5aea1ab302f
- http://ora.studiolegalebasili[.]com/gate_cb8a5aea1ab302f0_c
- http://ora.studiolegalebasili[.]com/gate_cb8a5aea1ab302f0_b
- http://ora.blindsidefantasy[.]com/gate_cb8a5aea1ab302f0_c
- http://rxc.rxcoordinator[.]com/gate_cb8a5aea1ab302f0_c
- http://pub.welcometothepub[.]com/gate_cb8a5aea1ab302f0_c
- http://ora.carlaarrabitoarchitetto[.]com/gate_cb8a5aea1ab302f0_c
- themoil[.]site
- ora.carlaarrabitoarchitetto[.]com
- ora.studiolegalebasili[.]com
- rxc.rxcoordinator[.]com
- Ora.blindsidefantasy[.]com
- Pub.welcometothepub[.]com
- marta.martatovaglieri[.]it
Hashes:
Kindly refer link below for details of Hashes.
Countermeasures and Best practices for prevention:
- Do not download and install applications from untrusted sources [offered via unknown websites/ links on unscrupulous messages]. Install applications downloaded from reputed application market only.
- Install and maintain updated antivirus solution on android devices. Scan the suspected device with antivirus solutions to detect and clean infections.
- Prior to downloading / installing apps on android devices (even from Google Play Store), Always review the app details, number of downloads, user reviews, comments and "ADDITIONAL INFORMATION" section.
- Verify app permissions and grant only those permissions which have relevant context for the app's purpose.
- In settings, do not enable installation of apps from "Untrusted Sources".
- Exercise caution while visiting trusted/untrusted sites for clicking links.
- Install Android updates and patches as and when available from Android device vendors.
- Users are advised to use device encryption or encrypting external SD card feature available with most of the android OS.
- Do not download or open attachment in emails received from untrusted sources or unexpectedly received from trusted users.
- Avoid using unsecured, unknown Wi-Fi networks. There may be rogue Wi-Fi access points at public places used for distributing malicious applications.
- Confirm that the banking/financial app you’re using is the official, verified version.
- If anything looks awry or suddenly unfamiliar, check in with your bank’s/financial service provider's customer service team.
- Use two-factor authentication if it’s available.
- Make sure you have a strong AI-powered mobile antivirus installed to detect and block this kind of tricky malware if it ever makes its way onto your system.
- Refer to security best practices for mobile Phone users:
http://www.cyberswachhtakendra.gov.in/documents/Mobile_phone_Security.pdf
References:


